Summary:
I still continue to look at Magnitude now that I have managed to get it to drop a payload. I’m amazed at how different the flows appears to look each time. It is a lot more interesting to witness than Rig EK.
Currently Magnitude is still region locked and “private” however it is still very active in these regions and is certainly a big threat to anyone using an outdated version of Flash, Windows or IE.
Here I have four samples which all dropped the latest version of Cerber Ransomware. I have created a CSV which contains all the URL’s for easier copy pasting for IOC’s.
Background Information
I came across this article which contains very good information about Magnitude and is mostly still relevant.
Some hints as to how to deobfuscate Magnitude:
https://pcsxcetrasupport3.wordpress.com/2017/04/24/a-look-at-the-magnitude-exploit-kit-encoding/
Downloads (in password protected zip)
Note to trigger Magnitude you need certain conditions so I have used a proxy to achive this which may explain odd headers and IP addresses.
- 2017-Apr-26-Magnitude-Cerber– Four PCAP’s of Magnitude and Cerber
- 2017-Apr-26-Cerber-Ransomware – Three samples of Cerber
- 2017-Apr-26-Magnitude-Flows-CSV – Four CSV files for easy copy pasting of URL’s
Details of infection chain:
(click to enlarge!)
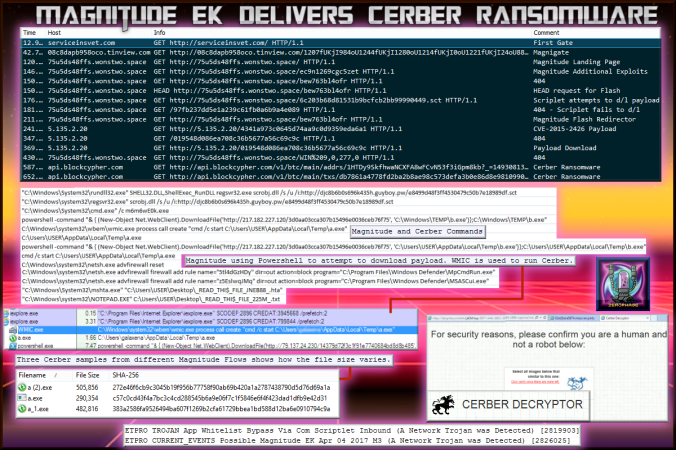
This image shows flows of the latest Magnitude sample. The commands are taken from another sample that is also included in the pcaps.
Full Details:
For more information on Magnitude check out my previous posts:
Magnitude EK URL’s from 14-20 April
I have Three samples of Cerber. I have been informed this is the latest version of Cerber. It did not change my background or play an audio. I would copy the hashes for easy copy paste but Cerber is very evasive when it comes to AV detections. The file sizes vary quite significantly between samples.
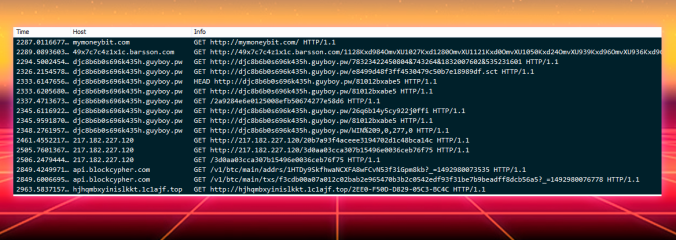
Cerber still attempts UDP 6893 connections. It also modifies firewall settings which you can see from the main image above. There is also a 5-10 min window in which the ransom ware actually takes effect.

These are the ransom notes .HTA and notepad file.
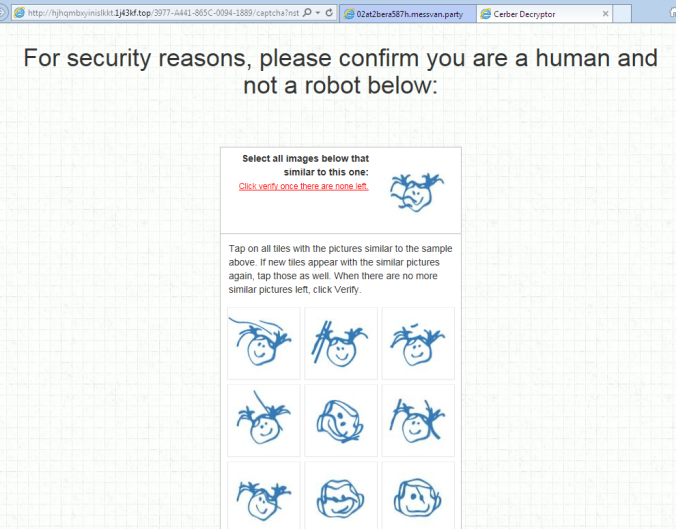
The Cerber Decryptor asks for a language. There are multiple not show here and the text cycles the languages.
It then asks to solve a captcha for a “security” check. I was unable to solve the puzzle so could not continue to the payment part.
Lastly this icon appears on the decryptor.




Hi, what is the password of the above 3 files ? I can’t open on it.
LikeLike
Password is – infected
LikeLike
Thanks 🙂
LikeLike
tried the password to unzip the archives, but doesnt seem to be working. Can you recheck once again.
LikeLike
I’ve just checked and it works for me with password – infected
They are ZIP files though if that makes any difference.
LikeLike
Pingback: Magnitude EK via Malvertising drops Cerber Ransomware | Zerophage Malware
Pingback: Magnitude EK via malvertising delivers Cerber Ransomware | Zerophage Malware
Pingback: Magnitude EK via RoughTed drops Cerber Ransomware | Zerophage Malware
Pingback: Magnitude EK drops “CBRB” (Cerber Ransomware) | Zerophage Malware
Pingback: Magnitude EK drops Cerber (Scriplet changed to “.bmp”) | Zerophage Malware