Summary:
Whilst the Petya variant ransomware campaign is occurring the use of WMIC reminded me of Magnitude EK which also uses it to run the payload. It’s also able to run PowerShell commands.
I hope to do a few learning tutorials on Magnitude in the near future mainly focusing on deobfuscation as it is vastly more complex than Rig EK. My current stumbling block is that I’m not entirely sure what the function of the 2nd part of the landing page is. If you know give me a nudge (its the “further exploits” part). It is not included in any articles that I have found.
This version of Cerber calls itself “CBRB” which is odd.
Background Information:
- Article from RSA, although a few months old and missing some newer aspects of Magnitude, the fundamentals have not changed.
- A few previous Magnitude EK posts from me.
Multiple Magnitude EK drops Cerber Ransomware Samples
Magnitude EK via malvertising delivers Cerber Ransomware
Downloads (in password protected zip)
- 28-June-Magnitude-Cerber-PCAP– PCAP of Magnitude and Cerber
- 28-June-2017-Cerber – Cerber (a.exe – efe238b3d28c819b27abe668d1188d7534101bcf9a1cfef0c7d56e33b00b8424)
- 28-June-Magnitude-Cerber-CSV – CSV of traffic with resolved IP addresses.
Full Details:
At some point I hope to take a deep dive into Magnitude EK, mostly focusing on deobfuscation. The first gate for example uses your “window.screen” object to generate the next URL and it’s quite interesting.
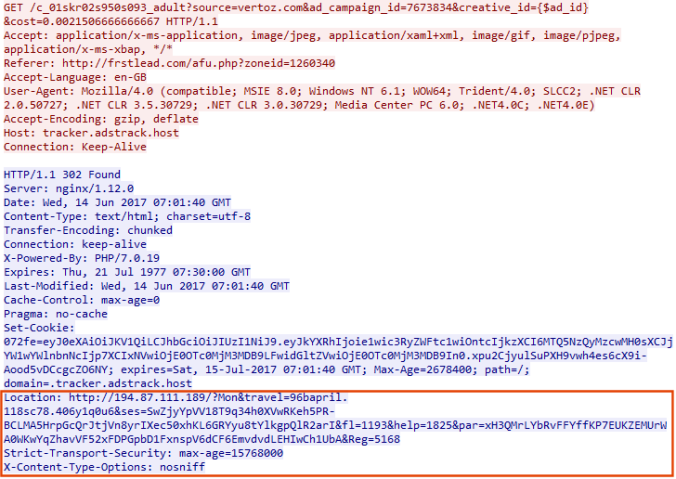
Although not shown in the main picture, a new trend for Magnitude is a double landing page which causes duplicate traffic.
For now here is a list of processes that were executed:
You can see the Scriplet is ran which drops 3 payloads all of which fail. I’m not sure why they fail but it’s possible that as the Flash request is one of the very first requests in the actual landing page and that Magnitude has already decided how to drop the payload and thus these fail. I will try it one day without Flash.
A PowerShell command is ran to download a file called “b.exe” and finally WMIC is used to run the payload “a.exe“.
The payload is of course Cerber Ransomware. This version calls itself “CBRB”.
When i submitted to VT it has relatively few detection’s and none directly refer to it as Cerber though some vendors may call it other things.
| SHA256: | efe238b3d28c819b27abe668d1188d7534101bcf9a1cfef0c7d56e33b00b8424 |
| File name: | a.exe |
| Detection ratio: | 13 / 61 |