Summary:
Another Bunitu sample from the same malvertising chain. It would appear the Flash detector, etc. is designed to catch bots as ad servers treat bots differently to real users. I do not think this script plays any role in funnelling the correct targets to Rig EK.
I do doubt the ad providers are purposely serving malicious content. However there is certainly a threat actor at work here who is using Rig EK to deliver Bunitu.
Background Information:
- A few articles on Rig exploit kit and it’s evolution:
https://www.uperesia.com/analyzing-rig-exploit-kit
http://malware.dontneedcoffee.com/2016/10/rig-evolves-neutrino-waves-goodbye.html
http://securityaffairs.co/wordpress/55354/cyber-crime/rig-exploit-kit-cerber.html
- Article on Bunitu Trojan:
https://blog.malwarebytes.com/threat-analysis/2015/07/revisiting-the-bunitu-trojan/
Downloads
- rigbunitu270217-> Contains pcapng and payload in password protected zip.
Notable Details:
- 188.72.202.219 – go.pub2srv.com[.]net – 302 redirect
- 206.54.163.4 – onclickads[.]net – Flash version detector
- 206.54.163.50 – onclkds[.]com – 302 redirect
- 104.197.27.232 – adexchangeprediction[.]com – 302 redirect
- 78.46.232.214 – sproutgames.info – iframe redirect
- 88.198.220.122 – sproutgame15[.]pw – Compromised Site iframe redirect
- 188.225.36.251 – lol.acemedicalsafety[.]com – Rig EK
- Payload was pawf85q6.exe -> VirusTotal
Details of infection chain:
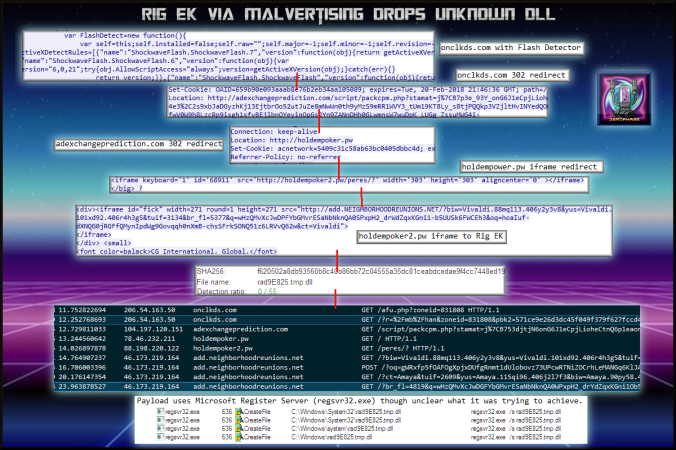
(click to enlarge!)
Full Details:
- A malvertising URL contains a Flash version detector as well as other scripts designed to catch bots.
- Two further 302 redirects.
- iframe redirect to compromised website.
- iframe to Rig EK.
- lol.acemedicalsafety[.]com -> Landing Page -> Flash -> Payload
- There was no Pre-Landing page as usually seen.
- Dropped payload “pawf85q6.exe” which is different to the usual “rad” themed ones.
-
SHA256: 06705f6df520256247e48c0da4ab81147761ef5091b012d9d5438e5121ef1187 File name: pawf85q6.exe Detection ratio: 10 / 58 - This was identified as Bunitu Trojan.
- Bunitu opens random ports by changing firewall settings and allows the host to become a remote proxy.
- Bunitu uses a DLL called nillvzs.dll.

Bunitu opens ports by changing firewall rules.