Summary:
I found this website through someone mentioning Rig EK so decided to analyse it to look for any new changes. The website contains the PseudoDarkleech gate.
My setup did not deliver Cerber ransomware however the Cerber Check In UDP traffic was observed again. I decided this time to save the payload before it terminated itself. I then put it through an online sandbox to see what would happen and found the exact same result.
The payload also created a strange “.8H” file which was not readable. I have been unable to find an answer as to why Cerber creates the UDP traffic. It is possible the payload has other functionality such as commands to a bot net to perform DDoS or the Emerging Threat signature is a not a false positive and it is an action of the infamous Conficker.
Background Information:
- A few articles on Rig exploit kit and it’s evolution:
https://www.uperesia.com/analyzing-rig-exploit-kit
http://malware.dontneedcoffee.com/2016/10/rig-evolves-neutrino-waves-goodbye.html
http://securityaffairs.co/wordpress/55354/cyber-crime/rig-exploit-kit-cerber.html
- Article on the PseudoDarkleech campaign and its history:
http://researchcenter.paloaltonetworks.com/2016/12/unit42-campaign-evolution-pseudo-darkleech-2016/
Downloads
- zerorigek190117 -> Contains Pcap, payload and interesting files in password protected zip.
Notable Details:
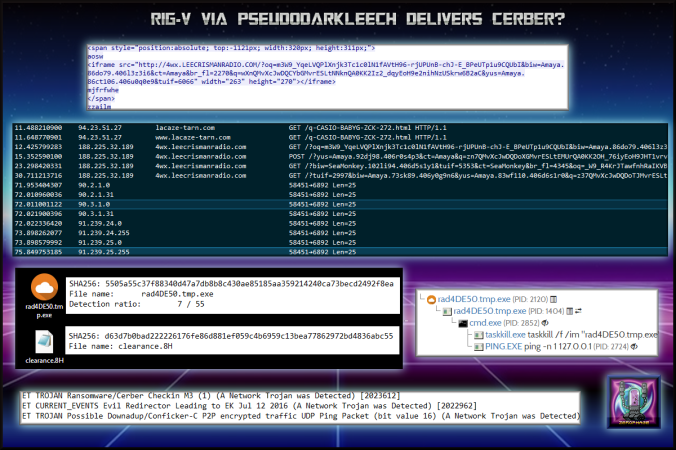
- 94.23.51.27 – lacaze-tarn[.]com – COMPROMISED WEBSITE
- 188.255.32.189 – 4wx[.]leecrismanradio[.]com – RIG-V
- 91.239.25.0/24 – UDP port 6892 – Cerber Check In IP Range
- 91.239.24.0/24 – UDP port 6892 – Cerber Check In IP Range
- 90.2.1.0 -> 90.2.1.31 – UDP port 6892 – Other UDP Traffic
- 90.3.1.0 -> 90.3.1.31 – UDP port 6892 – Other UDP Traffic
- Payload was rad92106.tmp.exe -> VirusTotal
- Conscious that I did not receive Cerber I also put it into HybridAnalysis which reported the exact same result.
- Also created a “.8H” file called “clearance“.
Details of infection chain:
Full Details:
- Compromised site redirects to Rig-V EK via PseudoDarkleech iframe.
- 4wx[.]leecrismanradio[.]com is Rig EK, from top to bottom -> Pre-Landing -> Landing Page -> Flash exploit -> Payload
- UDP traffic port 6892 to 91.239.25.0/24 all contained the data”0ca5ea83d2eb008c170000026“
- Dropped payload “rad4DE50.tmp.exe“
- Payload terminated itself and then deleted itself but also created a “.8H” file called “clearance“.
- Emerging Threat signatures for Cerber and Conficker
- I have not ruled out that this could be an action of Conficker but many other researchers have received Cerber following the UDP traffic observed. I have also seen the same in the past and received Cerber.