Summary:
Malvertising leads to Rig EK on another “Poker” website. This is the same method used in my two previous posts with slightly varying parameters.
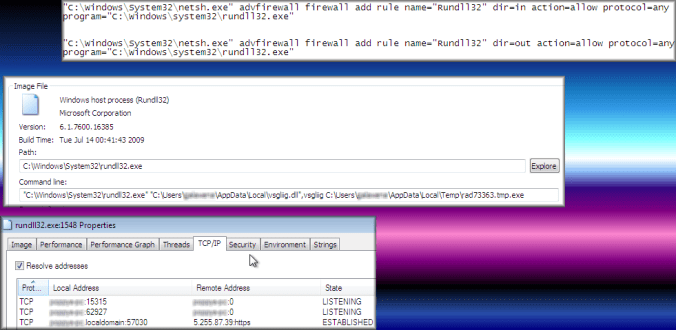
This time I could not identify the payload which appeared to be a DLL. It appeared to run and there was activity in processes but it made no network connections and did not seem to have changed the host significantly even after a reboot.
The DLL is available in the download below. If you have expertise in this area, I would be very keen to know what this file does or is supposed to do.
Background Information:
- A few articles on Rig exploit kit and it’s evolution:
https://www.uperesia.com/analyzing-rig-exploit-kit
http://malware.dontneedcoffee.com/2016/10/rig-evolves-neutrino-waves-goodbye.html
http://securityaffairs.co/wordpress/55354/cyber-crime/rig-exploit-kit-cerber.html
- Article from Malware Breakdown about Hookads. Similar to these infection chains:
Downloads
- 200217rigunkdll-> Contains pcapng and payload in password protected zip.
Notable Details:
- 206.54.163.50 – onclkds[.]com – Flash version detector
- 206.54.163.50 – onclkds[.]com – 302 redirect
- 104.197.120.151 – adexchangeprediction[.]com – 302 redirect
- 78.46.232.211 – holdempoker.pw – iframe redirect
- 88.198.220.122 – holdempoker2.pw – Compromised Site iframe redirect
- 46.173.219.164 – add.neighborhoodreunions[.]net – Rig EK
- Payload was rad9E825.tmp.dll -> VirusTotal
Details of infection chain:
(click to enlarge!)
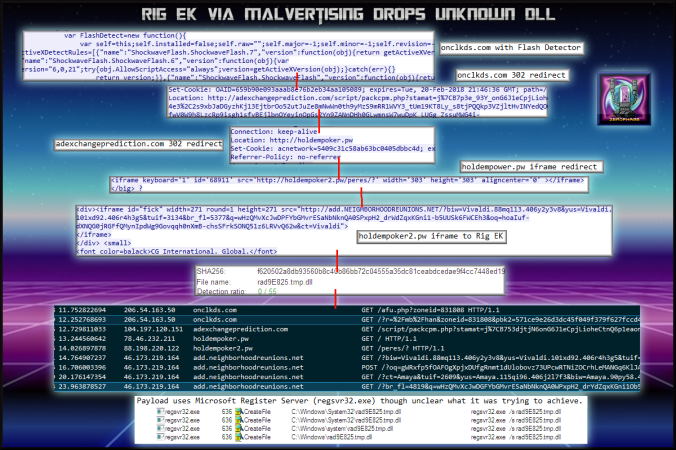
Malvertising chain leads to Rig EK which drops a DLL which did not appear to be make any noticeable changes.
Full Details:
- A malvertising URL contains a Flash version detector.
- Two further 302 redirects.
- iframe redirect to compromised website.
- iframe to Rig EK.
- oadd.neighborhoodreunions[.]net -> Pre-Landing -> Landing Page -> Flash -> Payload
- Dropped payload “rad9E825.tmp.dll” which came back 0/54 on VT.
-
SHA256: f620502a8db93560b8c40b86bb72c04555a35dc81ceabdcedae9f4cc7448ed19 File name: rad9E825.tmp.dll Detection ratio: 0 / 54
- The payload ran using regsvr32.exe and although there was some activity it did not appear to do anything significant. Perhaps it required a different version of Windows or maybe it made several subtle but important changes. I’ll keep monitoring the machine for any strange activity.
- The website at 78.46.232.211 appears to have host multiple Poker themed websites. The IP is the same as the previous Bunitu infection but domain is different.